4.1.1
Which of the following is not an advantage of storing data using cloud computing?
Prevents loss of data due malfunction of user’s personal computer.
This is a main advantage of cloud computing.
Easy to scale up from individual use to implementation by large companies.
This is a main advantage of cloud computing.
Has potential to be environmentally friendly due to many users efficiently sharing large systems and resources.
This is a main potential advantage of cloud computing.
Improved security and privacy over storing data on a personal computer.
Correct. With cloud computing, you are trusting someone else with your data.
4.1.2
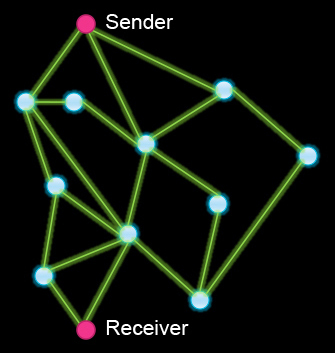
In this model of a network, what is the
minimum number of nodes (connection points) that can stop working before the sender and the receiver can't communicate? (Other than the sender or the receiver themselves, of course.)
1
There are no nodes that are vital to the system. Pick any node to stop working, and you can still find another path.
2
Correct! If the node with six connections goes down and also either of the two to its left, the sender and receiver can't communicate.
3
Try to find a smaller number of nodes that can stop working and still break communication.
4
Try to find a smaller number of nodes that can stop working and still break communication.
5
Try to find a smaller number of nodes that can stop working and still break communication.
4.1.2

In the same model network, what is the
maximum number of nodes that can fail and still let Sender and Receiver communicate?
10
Draw a path from sender to receiver that still works.
9
Draw a path from sender to receiver that still works.
8
Correct! If the four nodes on the right and also the four nodes on the left all fail, the remaining two nodes in the middle will still allow the sender and receiver to communicate.
7
Try to find a higher number of nodes that can stop working and still permit communication.
6
Try to find a higher number of nodes that can stop working and still permit communication.
4.2.5
Which of the following are existing vulnerabilities of the Internet, according to experts?
A physical attack that involves cutting fiber-optic cables.
Yes, but there may be more!
Attacking electrical systems that control the energy grid.
Yes, but there may be more!
Eroding the trust and confidence that the general public has in their online privacy and secure online transactions.
Yes, but there may be more!
4.4.1
Which of the following CANNOT be expressed using one bit?
The state of an ON/OFF switch
This has two possible states so a single bit is enough.
The value of a Boolean variable
This has two possible values TRUE/FALSE, so a single bit is enough.
The remainder when dividing a positive integer by 2
There are two possible remainders 0 or 1, so a single bit is enough.
The position of the hour hand of a clock
Correct. The hour hand spans a range of values between 1 to 12 so one bit is not sufficient. It will actually require 4 bits.
4.4.2
A particular online retail company uses 9-bit binary sequences to identify each unique product for sale. Expecting to increase the number of products it sells, the company is planning to switch to 10-bit binary sequences. Which of the statements below best describes the consequence of using 10-bit sequences instead of 9-bit sequences?
Two more products can be identified uniquely.
Compute how many products can be identified before and after the change.
Ten more products can be identified uniquely.
Compute how many products can be identified before and after the change.
Twice as many products can be identified uniquely.
Correct. Before 29=512 products could identified and now 210=1024 products can be identified.
Ten times as many products can be identified uniquely.
Compute how many products can be identified before and after the change.
4.4.5
A particular program uses 4 bits to represent whole numbers. When that program adds the numbers 9 and 7, the result is given as 0. Identify the best explanation of the result.
Data was corrupted during the operation due to a technical glitch.
While data corruption is possible, it is not a likely explanation for the recurrence of the result as one can demonstrate with repeated attempts to add 9 and 7.
The result was due to a round-off error.
There is no rounding done here.
The result was due to an overflow error.
Correct. 9+7=16, which is beyond the capacity of 4 bits to express. 0=(0000)2 is the first and 15=(1111)2 is the last integer expressible in a 4-bit system. 16=(10000)2 leads to an overflow.
A floating-point representation was used to approximate the result.
0 is not an approximation of 16.
4.4.6
A film student records a movie on his smartphone and then saves a copy on his computer. He notices that the saved copy is of much lower image quality than the original. Which of the following could NOT be a possible explanation for the lower image quality?
The movie was saved using fewer bits per second (a lower bit rate) than the original movie.
This is likely what happened. Which one could NOT be a possible explanation?
The copy of the movie file was somehow corrupted in the process of saving.
This is possible; however if the file is corrupted, it is unlikely to have a consistent negative impact on image quality.
The movie was saved using a lossy compression technique.
This is very likely. Which one could NOT be a possible explanation?
Whenever a file is saved from one computer to another, some information is always lost.
Correct. It is possible to make exact duplicates of digital information without any loss.
4.4.6
A visual artist is processing a digital image. Which of the following describe a lossless transformation from which the original image can be recovered? Choose two answers.
Creating the negative of an image, where colors are reversed (dark areas appear light).
Correct. This transformation is reversible and is an example of a lossless transformation.
Blurring the edges of an image.
The blurring blends colors at the edges of the image and once colors have blended it is impossible to retrieve the original RGB values of the pixels involved.
Creating a grayscale copy of an image.
The grayscale of an image replaces each RGB value with their average and once the amounts of red, green, and blue have been averaged together, it is impossible to retrieve the original RGB values of the pixels.
Creating a vertically flipped copy of the image.
Correct. This transformation is reversible and is an example of a lossless transformation.
4.4.6
For which of the following kinds of data would lossy compression be okay? Check as many as apply.
The HTML code for this web page.
Would you be happy if some of the words on the page disappeared?
Your computer's desktop picture.
Correct. The picture could have a few wrong pixels and would still look okay.
A live-action movie on Netflix.
Correct. The movie could have a few corrupted frames and would still look okay.
A cartoon on Netflix.
Actually, corrupted frames are more noticeable in a cartoon, which has solid areas separated by sharp edges. (Fortunately, using techniques such as run length encoding, it's relatively easy to get a lossless, highly compressed version of a cartoon.)
A digital book, to be read on a computer.
Digital books aren't stored as pictures, but as text. Any error will be noticeable, as gibberish characters on the page.
 In this model of a network, what is the minimum number of nodes (connection points) that can stop working before the sender and the receiver can't communicate? (Other than the sender or the receiver themselves, of course.)
In this model of a network, what is the minimum number of nodes (connection points) that can stop working before the sender and the receiver can't communicate? (Other than the sender or the receiver themselves, of course.)